Internet Explorer (despite what the average Linux devotee will tell you) is
not inherently insecure. It's as secure as Microsoft can possibly make it,
and is constantly updated to protect against new exploits and malware. It
does have the distinction of being the largest and most obvious target for any
Internet-based piece of nasty software though, meaning that new vulnerabilities
are constantly being discovered. Also, unlike competing browsers, IE is an
integral part of the Windows operating system, and thus can compromise the
entire computer if its security is defeated. In these respects, claims
that browsers like Firefox are inherently more secure than Internet Explorer are
correct.
This fact may be about to change though, since Microsoft is making some
fundamental changes to the way that Internet Explorer works 'under the
hood.' Let's take a look at some of the new security measures
The 'malformed URL' attack, in which the user is persuaded to click a link to
a URL that is intended to cause a buffer overflow in the browser's memory space,
allowing arbitrary (malicious) code to be executed on the computer, is one of
the most common attacks aimed at any browser. In current versions of
Internet Explorer, a patch needs to be devised to address each exploit of this
type, since the original browser code which contains the base vulnerability
cannot be easily changed.
Internet Explorer 7 is designed to reduce this vulnerability by providing a
single code location for processing URLs. This should not only make the
browser immune to all current URL exploits, but also make securing it from
future ones much easier to achieve.
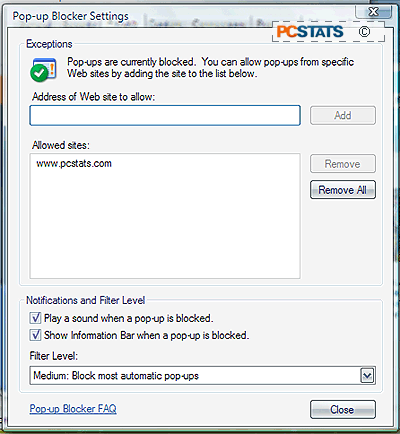 A second improvement to general Internet security is the IE 7 requirement
that all browser windows have address bars, providing users with more knowledge
about the web page they are viewing. This goes hand-in-hand with upcoming
(scheduled for Internet Explorer 7 beta 2) features which will allow users to
test whether the URL they are seeing in their address bar or in a link actually
goes where it says it does. This will hopefully neutralize one of the most
effective malware vectors: misleading or disguised links.
A second improvement to general Internet security is the IE 7 requirement
that all browser windows have address bars, providing users with more knowledge
about the web page they are viewing. This goes hand-in-hand with upcoming
(scheduled for Internet Explorer 7 beta 2) features which will allow users to
test whether the URL they are seeing in their address bar or in a link actually
goes where it says it does. This will hopefully neutralize one of the most
effective malware vectors: misleading or disguised links.
Microsoft has also made changes to the way scripts initiated by a website are
handled. The new restrictions allow scripts to be executed only within the
originating website's domain. To enable this, the domain name will be
appended to the script within IE7 and the browser will refuse to run
cross-domain scripts. This prevents certain phishing attacks in which a
user is tricked into browsing to a malicious web page which will then link to an
authentic protected site while simultaneously running a script to capture any
information the user enters into the site.
On the more technical side, Internet Explorer 7 should feature improved
support for CSS (Cascading Style Sheets) as well as new support for transparent
PNG graphics files, allowing a variety of transparency-related graphical effects
to be rendered more easily.
