Since this guide deals with the
creation of Virtual Private Networks within the various Windows operating
systems, we will deal in detail only with the two VPN implementations that
Microsoft supports, "Point to Point Tunneling Protocol "(PPTP) and "Layer Two
Tunneling Protocol with IPSec" (L2TP/IPSec).
First,
let's have a look at the aptly named Point to Point Tunneling
Protocol
Currently
the most common method of Virtual Private Network connection, and certainly
the easiest to set up in a Windows environment is Point to Point Tunneling
Protocol (PPTP). Microsoft's implementation of PPTP uses the Point-to-Point
Protocol (PPP) to initially encapsulate the data, then encrypts this with
Microsoft's Point-to-Point Encryption (MPPE). Authentication is provided by
Windows' built in dial-up authentication protocols; MS-CHAP, MS-CHAP v2
(Microsoft Challenge Handshake Authentication Protocol) and EAP (Extensible
Authentication Protocol).
These protocols provide a means
of authenticating both the client and the VPN server by means of a
user name and password, in the case of MS-CHAP, or a computer certificate or smart card
in the case of EAP.
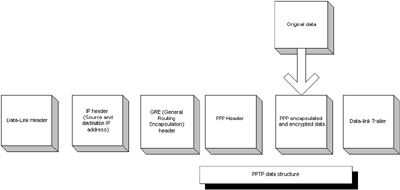
Once the data is encrypted, it is encapsulated again, this
time inside a GRE (Generic Routing Encapsulation) packet, which provides the information necessary to transmit
PPP information over the Internet. We now have the original data encrypted
and enclosed within a Point-to point protocol data packet, then further encapsulated within
a GRE packet for transmission across the Internet. To successfully transmit the data, two
more layers must be added.
First, an IP header containing the source and destination IP addresses is
constructed, then finally a data-link header and trailer appropriate to the type
of network being used. In the case of the internet, an Ethernet header with the
appropriate MAC addresses for the local network interface and the gateway. PPTP
uses a separate, unencrypted command channel to carry the commands used to open,
close and maintain the connection. This uses port 1723 on the server, and a
dynamic port on the client.