Another option which may be available is client filtering, which is sort of a
reverse firewall, blocking clients inside the network from accessing certain
ports. This can help you take control of your network, and prevent virus and
trojans from wreaking havoc if a computer does happen to get infected through an
errant email attachment. A reverse firewall is also incredibly useful at
preventing users of your network from accessing illegal websites (say
file sharing or adult content), or websites like Facebook.com which lead to a lot
of wasted hours when work just doesn't get done. Quite a few government offices
use this aspect of their firewall to prevent staff from accessing Facebook,
apparently after managers noticed hours and hours of union-wage saleries being
spent on the viral social networking website. At least, that's how we've heard
the story.
In any case, all of these methods use essentially the same forms of
information: port numbers.
Once you get used to the idea of ports as the way applications get
information in and out of your computer, configuring these options are simple.
Port mapping requires the identification of a machine on your network by name or IP address, a port to be accessed on that machine, and a port to be accessed on your firewall, and the type of protocol (TCP or UDP).
Special application exceptions require a 'trigger port' which sends data out
from that application, and one or more receiving ports, depending on the
requirements of the application.
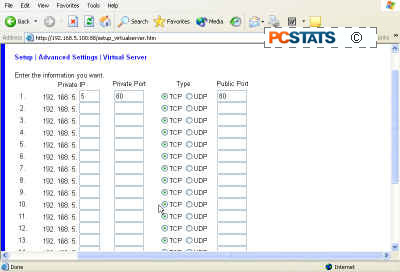
TCP or UDP must also be specified.

