The external port # identifies the port which users outside the network will
be allowed to connect to, and the internal port # specifies the port which will
be accessed inside the network if the application is running on a different
computer than your firewall system. This is called port mapping, the process of
passing information from a port on the Internet side of a firewall to a port in
the protected internal network.
All you need to know to create your own service is the port # that the
application you want to give access to, and whether the protocol it will accept
is TCP (connection oriented) or UDP (connectionless).
To simplify things, use the same port # for both internal and external ports.
A list of common applications and the ports they use can be found at the end of
this article. See below for an example of a custom service. One nice thing about
the XP firewall is that it will custom configure itself for certain Microsoft
applications such as MSN Messenger.
Creating Exceptions with the SP2 Firewall
If you have applied Service Pack 2, the XP firewall
works a little differently. Instead of needing to create a service for
each program that wants to allow connections through the firewall, you can
create an exception which allows that specific program to act as a server and
open the ports it needs. To create exceptions, go to 'start\control
panel\Windows firewall' and click the 'exceptions' tab.
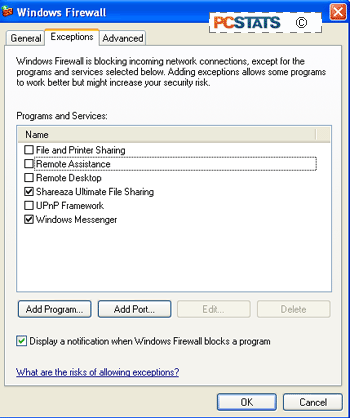
You'll see a list of programs and services. To
grant an exception, which will allow a program to open ports through the
firewall so that computers from the Internet can communicate with it, simply
place a check next to the program. If the program you need is not on the
list, click 'add program' and select it from the list.
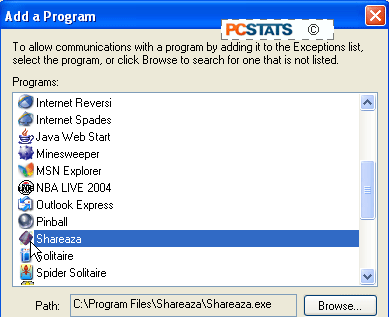
Most of your firewall configuration needs should be met
using the exceptions tab. If you need to grant special permissions to a
Windows service like IIS or FTP, you are better off using the services screen,
as directed in the above section.
Blocking exceptions with the Service Pack 2
Firewall
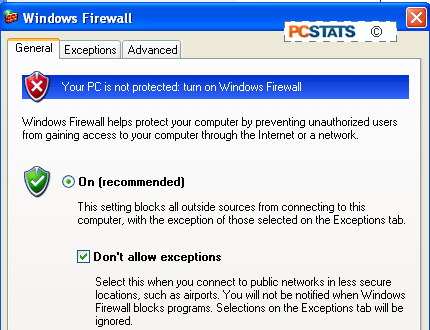
One new option you may wish to consider with XP's now
upgraded firewall software is the ability to block all exceptions, effectively
preventing any program or service in your computer from accepting outside
connections. This overrides the 'exceptions' tab and will stop programs
such as Kazaa from operating properly, but will absolutely prevent any malicious
software from acting as a server and compromising your data. To set this
option, go to 'start\control panel\Windows firewall' and check the 'don't allow exceptions' box.
Setting up a Home based cable/DSL router
firewall:
This set of instructions is a lot less specific than the XP firewall section, since there are such a variety of firewall equipped home routers on the market, using different interfaces. For the article, I used an SMC Barricade 4 port wired/wireless router, but the specifics should be similar for every router, they will just be configured differently.
Remember, on home routers, the firewall is enabled by default, so if you do not have a custom configuration to do, you can plug it in and go.
To start with, log into your router's management interface. Generally, entering your router's IP address into a web browser does this. See the manual if you have doubts.
Almost all home routers use NAT (Network Address Translation) as their firewall method. This is a combination of the functions of a circuit level gateway (internet sharing, recording requests from inside the network and denying all data from outside the firewall that does not match a request) and a packet filter for allowing or denying individual ports.
Depending on the model, you will have various levels of function. All router firewalls will, by default, stop unsolicited data from entering the network. They will also contain some form of port mapping to allow computers from the Internet to access specified applications within the firewall.
Some applications may require the use of multiple ports simultaneously, which
is not possible in a conventional NAT firewall. To get around this, some routers
and firewalls can create special application exceptions which define a 'trigger
port,' the port at which the application will initiate communication, then a
range of other ports which an application using the trigger port will also be
allowed to access.

