The cure: Set effective passwords for all users
The best way to protect yourself from malicious
users is to effectively password protect all your user accounts. An
effective password, according to Microsoft, is at least seven characters long and
contains a mix of upper and lower case letters, numbers and symbols. While you
can cut corners a bit here in the interests of memorization, make sure to use
six or more characters and include at least some numbers and upper case letters
in the middle of the word. By using several characters and a mix of upper and
lower case letters and numbers, you can make your password effectively
uncrackable to intruders who do not possess super computers capable of predicting
the weather...
To change
user passwords make sure you are logged in as a user with administrative privileges
(the first user created during the XP install process has these).
Right click on 'my computer' and select 'manage.' Expand
'local users and groups' then 'users.'
Right click on each user and select 'set
password.'
Note the ominous warning message. If you have
used XP's built-in file encryption to protect any of your files, you must remove
it before you change your password or you will lose access to the files.
Otherwise, proceed and set a secure password for each account.
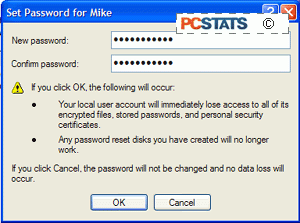
The accounts you should set passwords for are the
administrator account, and any accounts you created during or after the
installation of Windows.
Step 2. Make sure your system is protected by a
firewall
The Danger: Malicious users may locate and
attempt to break into your computer from the Internet.
The Cause: All computers that communicate over the Internet
must have a valid IP address, such as 61.232.252.6. These addresses allow
computers to exchange data with other computers over the 'net. Your system
also leaves a variety of ports open to listen for incoming data. Ports are
access points for certain kinds of data to enter and leave your computer.
For example, while you are viewing this website, your computer and our web
server are communicating through port 80, the default port for the HTTP language
that web pages generally use.
The
trouble is that anyone can use freely available software like GFI's LANguard security scanner to scan a range of IP addresses
for computers and gather information about these systems. If your
computer is poorly password protected these utilities provide remote users with the
ability to directly access your files.
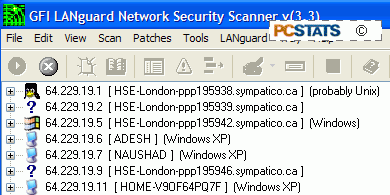
This happens because by default, many ports in your
system are fully prepared to listen and respond to any data request from the
Internet. This means that your system is fully visible, the equivalent of
wearing glow-in-the dark clothes in a blackout…

