
|
Firewalls are a necessity, but configuring them so that every internet-based program still works is often troublesome. With this guide, you can have your Firewall, and MSN File Transfers too.
|
|
|
|
Home >
Reviews >
Beginners Guides >
PCSTATS |
|
|
Strengthening Home router firewalls
This is a tricky subject, as
there are a wide variety of possible settings, and not every home router will
have certain options. What we will do is give you a list of potential settings
and what they can do for your firewall's security. Compare these to your
devices' documentation and configuration to ensure that you are fully
secured.
Block ICMP traffic, or 'stealth' mode: Not every
home router comes set to reject ICMP traffic by default. ICMP is the protocol
used most commonly by the PING program, which queries a given IP address and
reports back if a computer answers. This program forms the basis for the myriad
of 'scanner' programs freely available on the Internet. These scan a range of IP
addresses for responding computers. The systems that answer back to the ICMP
request are then targeted by the scanner for further, more intrusive measures to
discover security weaknesses. If your firewall blocks ICMP traffic, your system
is effectively invisible to casual Internet snoopers.
Stateful packet inspection: Certain firewall
products may feature stateful packet inspection as an option. This firewall
method takes a deeper look at each data packet received, instead of just
approving or dropping them based on the set rules of the firewall (allow x data
from y computer on z port). A stateful firewall will compare a data packet to
others received previously, and will also examine the full contents of the data.
This enables them to prevent attacks that traditional firewalls would not catch,
such as a DoS (Denial of Service) attack made up of massive amounts of identical
data packets intended to overwhelm the target system.
Disable remote administration: Most home routers
have a feature whereby the configuration screens can be accessed from the
Internet with a username and password. Obviously, disabling this feature
increases the security of your setup, especially since the devices ship with a
default password which many users forget to change.
Attack detection: Many home routers have a feature
where they specifically identify and log certain common types of attack, like
denial of service attacks or certain well-known exploits.
Disable file and printer sharing: This one should
be on by default with most home routers, if it exists at all, but check just to
make sure. When on, file and printer sharing allows remote users to access
shared files and devices on your system.
Configuring your firewall for common
applications
Now that your firewall is set
up correctly and configured for maximum security, it's time to make sure that
the Internet applications you commonly use play nicely with your newly secured
and firewalled internet connection.
Firewalls can play havoc with
certain programs that need unhindered access to several ports to carry out their
duties. One good example is the file transfer feature found in popular instant
messaging programs like MSN Messenger and ICQ. Peer-to-peer file sharing
programs like Kazaa and Shareza can also be affected, as can Internet-connected
multiplayer games.
Fortunately, allowing access
for these programs is generally simple, especially if you are using a software
firewall like the XP firewall or Zonealarm. Hardware devices can be a little
harder to work with, but it's still generally easy to get around.
The most difficult step in
this procedure is actually discovering which ports need to be opened for certain
programs. Generally this information can be obtained fairly easily by visiting
the website of your software's manufacturer, but there are alternative methods.
The easiest of these is to download a tiny freeware program called TCPview by Sysinternals. This excellent little utility gives you a graphical,
realtime view of all active connections on your system. If a program on your
system connects to the Internet, TCPview will tell you and show the port it's
using.
Let's look at how to use the program.
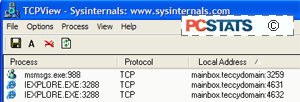
Upon running TCPview, you will
be greeted with a screen full of information. Very overwhelming.
This is because by default, the software lists all
listening ports as well as those that currently have connections. To cut the
view down to something more manageable, open the 'options' menu and uncheck the
'show unconnected endpoints' option.
Much better.
Assuming you have your browser
open (and if you don't, how are you reading this...?) you should see one or more
lines with the identity of your browser on the far left. Each of these lines
represents an active connection between your computer and a remote host.
The third column 'local address' shows the name of
your computer and the port number that is being used for that particular
connection. So 'mainbox:4356' indicates that that particular connection is using
port #4356. Experiment by opening up new browser windows or chatting on an
instant messaging program.
Using this utility, you can determine what ports any software needs by
running the software and noting down the connections that it makes. Of
course, you will need to deactivate your firewall during this process, so that
it does not prevent the connections from being made. For the WindowsXP and
Zonealarm firewalls, you can easily deactivate or close them, but for home
router firewalls, you will need to either disable the firewall within the
device's configuration (if the option exists) or connect your PC directly to
your DSL or cable modem while you are testing. Let's take a look at
configuring our three firewall examples for a variety of common applications.
Even if your chosen Internet software is not represented here, you should be
able to figure out the necessary process from these instructions.
|
< Previous Page
|
© 2025 PCSTATS.com
Please respect the time and effort that went into creating each PCSTATS Beginners Guide, do not illegally copy. Thank you.
|
Next Page >
|
|

